Massive 2.7B record breach leaks 272M SSNs: National public data hack sparks identity theft crisis

- A massive cybersecurity incident exposed nearly 2.7 billion unencrypted records, including names, addresses, and social security numbers, affecting millions in the US.
- Threat actors leaked the stolen data for free on hacking forums after an initial $3.5 million sale attempt, sparking widespread fraud risks.
- The breach led to class-action lawsuits and the company’s bankruptcy filing, highlighting vulnerabilities in data aggregation practices.
In the shadowy corners of the dark web, where cybercriminals trade secrets like commodities, a colossal data breach has unfolded that could redefine the landscape of personal privacy and cybersecurity threats.
Imagine waking up to find your most sensitive information—your name, every address you’ve ever called home, and even your social security number—freely circulating among hackers eager to exploit it for identity theft or phishing scams.
This isn’t a hypothetical nightmare; it’s the reality stemming from the National Public Data hack, a breach that has already sent shockwaves through millions of lives and raised urgent questions about how companies handle vast troves of personal data.
The story begins with National Public Data, a Florida-based firm operated by Jerico Pictures Inc., which specialized in aggregating public records for background checks, criminal history lookups, and services used by private investigators and employers.
Founded by former sheriff’s deputy Salvatore Verini Jr., the company scraped information from various public sources to build comprehensive profiles on individuals across the US, UK, and Canada.
But in December 2023, hackers infiltrated its systems, siphoning off an enormous database that would later be valued at millions on the underground market.
Initial reports pegged the haul at 2.9 billion records, but the leaked version contained about 2.7 billion plaintext entries—none of them encrypted, making them immediately usable for malicious purposes.
Massive #DataBreach Alert ⚠️
— HackManac (@H4ckManac) April 8, 2024
2.9 billion records of USA, Canada, and UK citizens allegedly for sale for $3.5 million.
The threat actor USDoD claims to be selling a 4 TB database containing 2.9 billion rows apparently exfiltrated from National Public Data, a public records data… pic.twitter.com/kgSd3RpoP2
What makes this breach particularly insidious is the involvement of notorious threat actors.
In April 2024, a hacker known as USDoD—a figure previously tied to attempting to sell the InfraGard user database for $50,000 in December 2023—boasted on dark web forums about possessing data on every person in the three countries.
USDoD tried to auction it off for a staggering $3.5 million, claiming it included full names, social security numbers, mailing addresses, phone numbers, email addresses, and dates of birth.
Yet, the plot thickened when, on August 6, 2024, another actor named Fenice posted the most complete dataset for free on the Breached hacking forum, attributing the actual theft to a hacker called SXUL.
This free release democratized the danger, allowing anyone with basic technical know-how to download the 277GB files and mine them for exploitable details.
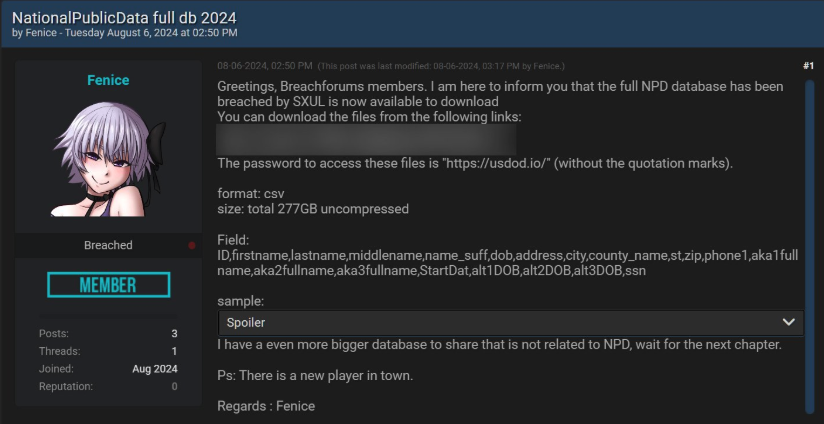
As experts dissected the leak, patterns emerged that amplified the alarm.
Each record typically featured a person’s name, multiple addresses (one for each known residence), social security numbers, and aliases like nicknames or maiden names.
Some entries even included alternative dates of birth, hinting at the database’s tolerance for inaccuracies to cast a wider net in background checks.
Cybersecurity researchers from firms like SpyCloud and VX-Underground verified samples, confirming the data’s authenticity for many users who checked their own information.
One chilling revelation: the leak encompassed details on deceased individuals, with the average age of affected people around 70, suggesting the data pulled from historical archives.
Pivoting through the dataset revealed duplications and errors—social security numbers mismatched to unrelated names or relatives—yet the sheer volume meant hundreds of millions were genuinely at risk.
Microsoft, in its guidance on the incident, noted the breach potentially exposed up to 170 million unique individuals across the US, UK, and Canada, with risks extending to physical threats from address leaks and increased spam from compromised phone numbers.

The human toll is already mounting. Individuals who searched breach-checking tools like Have I Been Pwned reported finding their full profiles, including old addresses from decades ago that could bypass identity verification systems.
On platforms like X (formerly Twitter), users shared stories of discovering their data online, with one post detailing how to opt out from the resurfaced National Public Data site under new ownership—now ironically offering a removal form that requires submitting even more personal details for verification.
Class-action lawsuits flooded in, accusing the company of negligence, unjust enrichment, and breaching fiduciary duties.
Plaintiffs demanded not just compensation but systemic changes: mandatory data encryption, regular cybersecurity audits, and third-party threat management for the next decade.
But as the lawsuits piled up, National Public Data crumbled. By October 2024, the company filed for bankruptcy, citing overwhelming liabilities from notifying and providing credit monitoring to potentially hundreds of millions of victims.
Court documents revealed investigations by the US Federal Trade Commission and attorneys general from over 20 states, all demanding civil penalties for the firm’s lax security.
A leaked back-end database password on the company’s homepage had fueled the intrusion, underscoring a cascade of preventable failures like outdated systems, weak authentication, and poorly secured APIs.
| Key Fact | Details |
|---|---|
| Total Records Leaked | 2.7 billion (plaintext, 277GB) |
| Unique Social Security Numbers Exposed | 272 million |
| Data Types Included | Names, addresses (historical and current), aliases, some phone numbers and emails in partial leaks |
| Breach Timeline | Infiltration: December 2023; Initial Sale Attempt: April 2024; Free Leak: August 2024 |
| Affected Regions | Primarily US, with claims of UK and Canada (unverified for full scope) |
| Company Response | No initial reply; later bankruptcy filing in October 2024 amid lawsuits |
| Potential Risks | Identity theft, phishing, synthetic identity creation, financial fraud |
Amid this chaos, cybersecurity experts warn of cascading effects.
The data’s fragmentation across dark web markets means fragments could fuel targeted scams—phishers using nicknames for personalized attacks or fraudsters blending real SSNs with fabricated details for synthetic identities.
Blade Technologies analysts pointed out how the breach weaponizes even public records when centralized and unsecured, urging reforms in data collection laws.
In 2025 updates, the Picus Blue Report highlighted a doubling in password cracking successes to 46% of environments, tying into broader trends of data exfiltration that this incident exemplifies.
For those caught in the crosshairs, protective steps are crucial yet frustratingly reactive.
Freezing credit with major bureaus like Equifax, Experian, and TransUnion can block unauthorized accounts, while enabling two-factor authentication and using password managers fortifies online defenses.
Services like Identity Guard or Microsoft Defender offer identity theft monitoring, scanning the dark web for exposed SSNs and providing up to $1 million in restoration insurance.
Regularly reviewing free credit reports and setting up transaction alerts on financial accounts adds layers of vigilance.
But beware: scammers are already capitalizing, impersonating authorities in investment frauds or tax schemes using the leaked details.
As the dust settles, one can’t help but wonder—what other hidden vulnerabilities lurk in the vast data silos we unwittingly feed every day, and how many more breaches will it take before true safeguards emerge to shield us from the next digital catastrophe?